My wife took a vow to put up with me 25 years ago today. Since then, she’s been my ride-or-die best friend through our many grand adventures. We didn’t always know how they’d work out. We’ve always gotten through them together. I know there’s nothing too big for us to face side by side.
Here’s to the next 25, my love, and all the others after that.
Project dream 1:
- Toss and turn all night, thinking of a million things to be done, going in deep to solve some hard problems.
- Wake up and remember none of that exists. Relax. Laugh.
Project dream 2:
- Same as above.
- Remember, oh yes it does.
- Desperately make notes before it goes all Xanadu to your Coleridge.
- Sit in a cold, panicked sweat for a little while.
It’s been a long week already, it’s Tuesday, and I haven’t even returned to work yet.
We survived Def Con. Barely. It was about as much fun as I’m physically able to tolerate in 1 week. Highlights:
- Meeting many online friends and finding out they’re all delightful in person.
- Seeing it all through my first-time-attendee wife’s eyes as we meandered through it all.
- Coordinating, conspiring, and scheming face-to-face.
- Being on the team taking 2nd-place in the EFF Tech Trivia contest.
- Oh yeah, the parties.
We’re both happy, grinning, utterly exhausted, energized, and ready for next year.
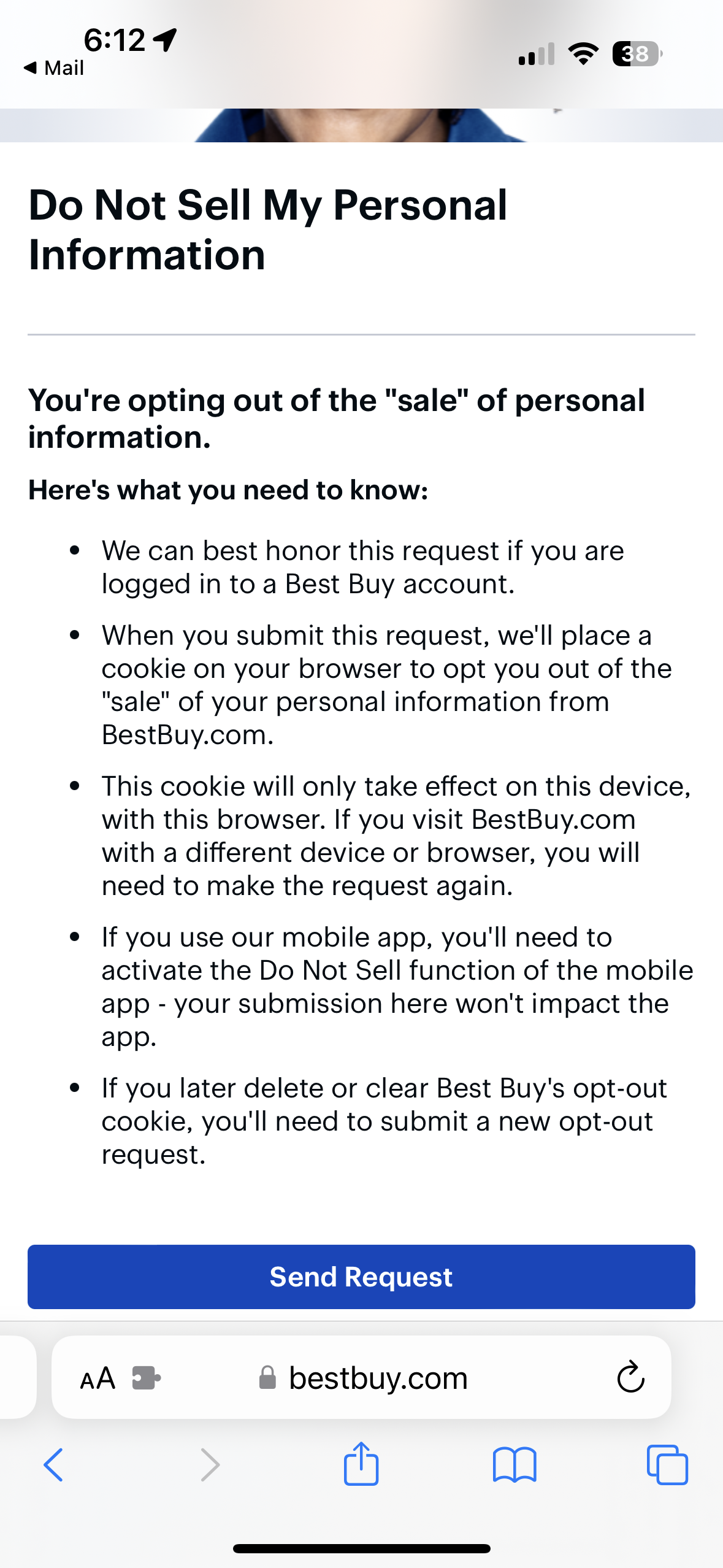
Best Buy’s new anti-privacy practices are even more awful than before. They’ve lost any business I’d ever be sending them after this.
Def Con badge acquired. Most of the way through the merch line; another 4 hours at most.

Hallway.

We made it to Vegas in 1 piece, ate a deliciously unhealthy lunch, checked in early (pro-tip: pay the $15 extra for a room upgrade if given the option), and set up the WiFi router that lets all our devices connect to the Internet at the same time without paying an arm and a leg every day.
It’s been a buy morning. Now we rest, re-caffeinate, and then hit the strip.
DEF CON is nearly upon us. Today we’re finishing our packing, checking into flights, finalizing plans to meet with friends, and twiddling our thumbs until it’s time to go to bed and wake up early.
Hope to see y’all there!
Amazon sent me an email about their new “Amazon One” service:
Amazon One is a fast, free identity service that allows you to pay using only your palm at all Whole Foods Market, Amazon Fresh, and Amazon Go locations. Your Prime member discounts will be automatically applied when you checkout at Whole Foods Market.
I was raised in an evangelical Christian household, as are somewhere around 25% of Americans. I can say with authority that a huge percentage of the US believes that paying with a “mark” on your hand, or forehead, is a certain indicator that the world as we know it is about to end. I do not believe this. I personally know plenty of people who do.
Things like this from a major brand always surprise me. I find it hard to imagine that the focus groups it surely went past didn’t have at least a few people saying “no, I won’t use this, because it’s literally the work of the Antichrist”.
My last work day before Def Con. I’m getting so excited and a little anxious! I’m going to see a lot, learn a lot, maybe teach some, and reunite with some of my favorite people in the world.
“Summer camp”, indeed.
The email: Click here to enhance your account’s security with two-factor authentication!
Click.
The website: Please enter your phone number to receive your access code.
Cmd-W.
My friends and I are getting ready for the EFF Tech Trivia contest at DEF CON. We took a year off after winning in 2022. Now we’re returning to reclaim our bragging rights.
If the cupboard door is open, Jort will sense it and come running from across the house so she can climb in among the towels.

Hi, person reading this who writes code that parses RSS or JSON Feed! Thank you for making neat tools that connect parts of the open Internet to each other!
But. Can you do me a favor, and gracefully handle a missing or empty optional title field? See the part of book.micro.blog/external-… about “No titles”. I think Manton Reece is 100% right about this. If a post doesn’t have a title, please don’t use the date or “Untitled” or (shudder) “Undefined”. Thank you!
So tell me about this dressage thing.
Well, a horse walks around.
Really fast?
No, just walking.
That’s it?
No, sometimes it stops for a little while.
It stops?
Yeah. Then walks backward.
Far?
No, just a little bit. Then it walks forward again.
Are you messing with me?
Nope.
Mleh.

Keeva became ill in the last week. I took her to the vet expecting she’d need some medicine and TLC. Instead we got some very bad news.
Our sweet girl – verifiably the best pup ever – is going to sleep tomorrow. She’ll be surrounded by a heartbroken family who loves her very much and will help her rest as comfortably as possible.
Goodbye, sweetie. I’ll miss you forever.

I’ve modified my Python program that sends new drafts from my Freewrite Alpha to my blog. Now it can also send them to my journal app, depending on what I type at the end of the message.
I like how it’s shaping up to work with the little keyboard. I’m turning it into the hardware version of Drafts: enter some text, decide what to do with it, let automation handle the details.
John Deere Dismissing 15% of Global Salaried Workforce Today | AgWeb:
Online sources say the layoffs cut across a wide swath of John Deere global corporate and administrative divisions and in total could affect 4,500 to 6,000 employees once complete.
Another large American company is on the edge of bankruptcy. I feel bad for their senior management, too, who must be devastated at their utter failure to lead it to success.
Either that, or they’re psychopaths who are crushing their workers to make an extra buck. I choose to give them the benefit of the doubt and assume they’re just bad at business.
I dusted off an older Raspberry Pi 4 to play with. Now I remember how glacially, painfully slow microSD cards are. This thing feels nearly unusable after being spoiled by its twin with an SSD.
If you use a Raspberry Pi for anything more than occasional goofing around, get an SSD. It makes it a new computer.