privacy
- Lacks end-to-end encryption
- Move to Folder
- Move to Trash
- Forward to
- Mark as Read
- Move to Folder and Mark as Read
- Move to Trash and Mark as Read
- Forward to an Email Address and Mark as Read
- If your phone detects that an AirTag is moving around with you, and its owner isn’t nearby, then the phone will warn you about it. That’s great if you’re being stalked, but terrible if it’s notifying a thief that there’s a tag in your backpack that they’ve just stolen.
- Inexplicably, Family Sharing doesn’t work for AirTags. I can’t help my wife find her car keys, even though we’re already using the “Find My” app to share our locations. If someone were coercing me to carry an AirTag around so they could track me, they could also coerce me into sharing my location with them through that same app.
- If I grab my wife’s keys for a quick trip to the grocery store, her AirTag on them will start beeping to alert me to its presence. That’s just silly; see the previous point.
- The latest iOS beta lets you manually scan for hidden AirTags, sure to be a favorite must-have feature among thieves.
- Enable a six-digit passcode on your device.
- Set your device to erase itself after 10 failed passcode attempts. You should do these two steps anyway!
- Before you get to airport security, turn your device off. iOS devices require a passcode to unlock themselves the first time after they’re turned on. For dumb legal reasons, passcodes are generally thought to be protected by the 5th amendment, but fingerprints are not.
- Turn on iCloud backup.
- When it’s finished backing up, reset your device to its factory settings.
- When you get where you’re going, restore your device from backup.
- Turn on iCloud backup.
- When it’s finished backing up, reset your device.
- Start using it. Add a few contacts. Set up a (disposable) email account. Add some songs.
- Turn on iCloud backup. Let it finish.
- Leave this device at home.
- When you get where you’re going, buy a replacement device. Restore it from the backup you made earlier. Now you have an exact clone of the original.
-
This isn’t meant as advice for criminals. Lots of people travel with information they’re legally obligated to safeguard, like company plans, legal documents, and other confidential information. ↩︎
-
Similar ideas apply for Android and other devices, but I don’t have one of those to experiment with. ↩︎
- You register for Facebook with your me@yahoo.com email address.
- You forget about that, read about the newest Yahoo user database hack, and delete your Yahoo account.
- A month later, someone else signs up to get your me@yahoo.com email address. They use Facebook’s password reset mechanism to take control of your account, download your private photos, and say nasty things to your friends.
- Oh, and anyone you forgot to share your new address with is still sending personal communications to your old Yahoo address, and its new owner is reading them.
- Read messages from your spouse or partner.
- See your calendar events to know when you’ll be away from the house.
- Take over your account and start resetting every password associated with it, like Facebook, Amazon, and your bank.
- Log into your Yahoo mail.
- Click the little checkbox above your emails to select all of them.
- Click the Delete button to delete all email on that page. If you have lots of messages, you may have to repeat this several times.
- Hover over the Trash mailbox to make the trashcan icon appear. Click the trashcan.
- Confirm that you want to empty your trash.
- Click the settings gear in the top right corner.
- Choose Settings, then Vacation Response.
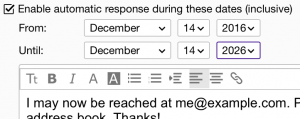
- Check the box to “Enable automatic response”, and set the Until: year to as far in the future as it will let you.
- Enter a message like:
- Click Save.
A Swift Cloud - Things Blog - Cultured Code culturedcode.com/things/bl…
This is so frustrating. Things is really neat, but they went through all the effort of rewriting its backend from scratch with no mention of end-to-end encryption. You just have to trust that they’re not selling your data, training AIs with it, giggling at your notes to buy flowers for your SO, or whatever. I’m pretty sure they’re not, but having to trust that they’re not is a dealbreaker.
How California sent residents’ personal health data to LinkedIn – The Markup:
As visitors filled out forms on the website, trackers on the same pages told LinkedIn their answers to questions about whether they were blind, pregnant, or used a high number of prescription medications.
Do not, ever, use a web browser without an ad-blocker. Even the FBI and NSA officially recommend it.
France Fines Apple €150 Million Over iOS Data Consent Rules - Bloomberg
Things like this are why it’s hard for me to take EU regulation seriously. (In before “but what about the US…” Yeah, I know.)
It’s purely good that Apple makes apps get your approval before allowing them to track your actions. France claims this is hard for the poor companies like Facebook that want to collect every move you make. Yes. It’s supposed to be. That’s the point. I want it to be.
AG Bonta reminds 23andMe customers of right to delete data
AG Bonta reminds 23andMe customers of right to delete data:
California Attorney General Rob Bonta issued a consumer alert Friday urgently warning the public that 23andMe is in financial distress and instructing customers on how to delete their data.
That’s good enough for me. I used 23andMe when it launched and love the promise of gaining medical insights from my own genetic data. That’s a powerful vision I still support. But given the lack of federal privacy protections on this most sensitive and personal of all data, I’d rather delete it than let some creep buy it in a fire sale.
Some friends and I got a pack of Orbic mobile hotspots so we can install the EFF’s Rayhunter software on them to detect “StingRay” IMSI-catchers. This is what one looks like.

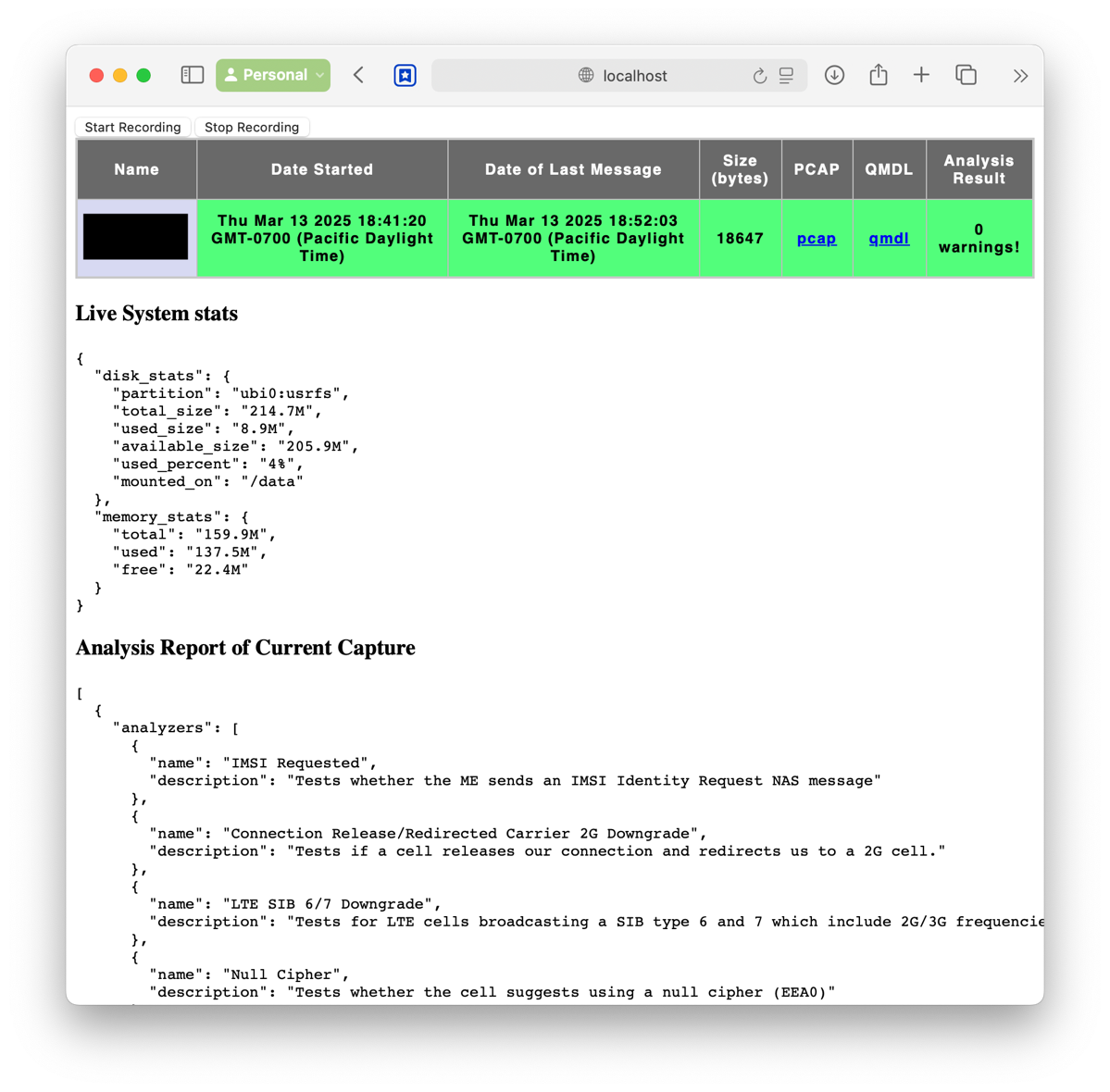
RIP Mark Klein
In Memoriam: Mark Klein, AT&T Whistleblower Who Revealed NSA Mass Spying
I moved in down the block from Mark when we first came to the Bay Area. One day he saw me getting out of my car and noticed my EFF hat. He asked if I worked for them, and I said I’m just a happy supporter. He told me they once helped him out of a bind and said I should look him up.
Mark was a super nice guy. He also had the world’s most aggressive golden retrievers that would bark at me as I walked down the block. One day I found a “sewer cleaning” van parked on the parallel street behind his house, but to this day I wonder what it really was. They drove off right after I took a picture of it.

Best Buy’s new anti-privacy practices are even more awful than before. They’ve lost any business I’d ever be sending them after this.
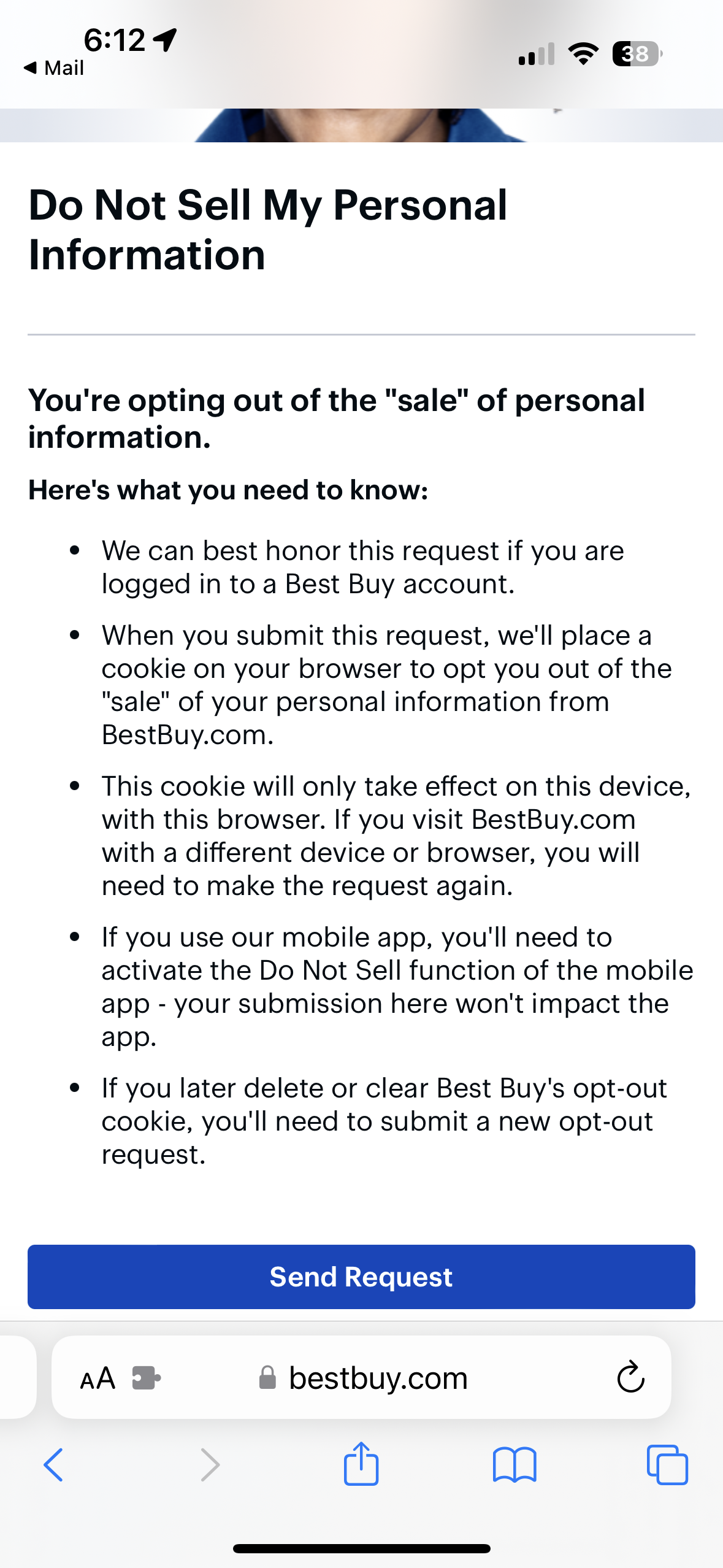
Demand that car companies respect your privacy
How to escape Honda’s privacy hell:
With sensors, microphones, and cameras, cars collect way more data than needed to operate the vehicle. They also share and sell that information to third parties, something many Americans don’t realize they’re opting into when they buy these cars. Companies are quick to flaunt their privacy policies, but those amount to pages upon pages of legalese that leave even professionals stumped about what exactly car companies collect and where that information might go.
So what can they collect?
“Pretty much everything,” said Misha Rykov, a research associate at the Mozilla Foundation, who worked on the car-privacy report. “Sex-life data, biometric data, demographic, race, sexual orientation, gender — everything.”
That’s despicable. Shame on you, Honda. Mozilla’s privacy report says their competitors are all pretty bad, too.
If you live in a state with a privacy law, you can and should write to your car’s manufacturer and demand that they show you all the information they collect about you, that they delete it all, that they not share it with anyone else, and that they limit how they use your data only to provide the services you’ve requested from them. These are your legal rights and manufacturers are legally obligated to respect them, even if it’s inconvenient and expensive for them. In fact, I think it’s our duty as citizens to make it cost companies more to process millions of our opt-out requests than they make selling our personal information.
TriNet shares employee PII without controls
My employer’s HR department asked me to validate a coworker’s identification documents and attest that they’re legitimate, for government tax form purposes.
I got an email from our payroll vendor, TriNet, with a link to attest to those documents’ authenticity. Clicking it took me to a page with scans of my friend’s driver’s license and Social Security card without requiring me to log in first. My coworker hadn’t entered their driver’s license number into the form, so I used the scanned image to enter it for them.
That’s pretty messed up. Good thing TriNet didn’t send that link to the wrong person, or they would have shared my colleague’s personally identifiable information with random strangers.
If your company uses TriNet, ask them for more information about this terrible, horrible, no good, very bad process, and how it got past design review. Their whole job is managing private payroll information. They’re not very good at it.
I use Things without encryption
Update 2023-11-03: No, I don’t.
I tell people not to use Readdle’s Spark email app. Then I turn around and use the Things task manager, which lacks end-to-end encryption (E2EE). That concerns me. I have a PKM note called “Task managers”, and under “Things” my first bullet point is:
I realize I’m being hypocritical here, but perhaps only a little bit. There’s a difference in exposure between Things and, say, my PKM notes, archive of scanned documents, email, etc.:
I don’t put highly sensitive information in Things. No, I don’t want my actions in there to be public, but they’re generally no more detailed than “make an allergist appointment” or “ask boss about a raise”. I know some people use Things as a general note-taking app but I don’t. There are other apps more tailored to that and I use them instead.
I control what information goes into Things. If my doctor were to email me sensitive medical test results, the Spark team could hypothetically read them. Cultured Code can only view what I personally choose to put into Things. (That glosses over the “Mail to Things” feature, but I never give that address to anyone else and I don’t worry about it being misused.)
Things can’t impersonate me. Readdle could use my email credentials to contact my boss and pretend to be me. Now, I’m confident that they won’t. They’re a good, reputable company. But they could, and that’s enough to keep me away from Spark.
Finally, Cultured Code is a German company covered by the GDPR. They have strong governmental reasons not to do shady stuff with my data.
While I don’t like that Things lacks E2EE, and I wish that it had it, the lack isn’t important enough for how I want to use it to keep me away from it. There are more secure alternatives like OmniFocus and Reminders, but the benefits that I get from Things over those options makes it worthwhile for me to hold my nose and use it.
Everyone has to make that decision based on their own usage. If you have actions like “send government documents to reporter” or “call patient Amy Jones to tell her about her cancer”, then you shouldn’t use Things or anything else without E2EE. I’d be peeved if my Things actions were leaked, but it wouldn’t ruin my life or get me fired.
But I know I should still look for something more secure.
Apple won't totally block unwanted emails
Apple’s email apps and services don’t allow users to completely block senders. If someone is sending you messages you don’t want to receive, tough. You’re going to get them.
The iCloud.com website’s Mail app doesn’t have a sender block mechanism. Instead, it offers a way to create rules based on each message’s attributes, such as its sender. Rules support these actions:
None of those actions are the same as bouncing or silently discarding an email. At most, you can have the email sent to your Trash folder.
Mail.app on a Mac allows you to mark senders as “blocked”. You can configure Mail.app’s junk mail filters to either “Mark [their message] as blocked mail, but leave it in my Inbox” or “Move it to the Trash”. Again, you can’t bounce or discard it.
I tried to be clever and write an AppleScript program to delete messages from my Mac’s Trash folder. That was a dead end because AppleScript’s idea of deleting an email is moving it to Trash, even if it’s already in there. Neither does it offer a way to automatically empty the trash.
Apple, this is disappointing. If I’m blocking someone, I don’t want to hear from them at all, ever. It’s not enough to send their messages to the Trash folder. I don’t want them to be in my email account at all.
Easily delete your Twitter account the hard way
The folks at Conscious Digital have a nifty website, yourdigitalrights.org, that makes it easy to file a CCPA or GDPR request asking a website to remove all of your data.
In particular, they make it easy to delete all your Twitter data.
Delete your account, regain your privacy, and cause someone an administrative hassle with a single click. It’s perfect!
Dealing with Princeton's flawed privacy research
This has been an odd week. Last Friday I got an email from someone asking about my hobby website’s CCPA compliance, ending with
I look forward to your reply without undue delay and at most within 45 days of this email, as required by Section 1798.130 of the California Civil Code.
The message sounded more legitimate than the usual spam I get, as it was asking about a real law in the jurisdiction where I live, and because it referred to a real website that I operate. That last line looked to my not-a-lawyer eyes like something a professional litigant might send out when they’re trying to gather information before deciding whether to sue someone. Mass frivolous lawsuits are a thing, after all, and I dreaded the idea that I might have had to defend my personal project in court.
This Friday, a friend told me that a researcher at Princeton sent the emails as part of a study on CCPA compliance they’re conducting with Radboud University. That changed my whole outlook: the letter came from a fake person with a fake email domain, lying about their intentions, and lying that the CCPA required me to reply to it. The stress it caused me wasn’t fake, though.
I submitted a link to my story to Hacker News, which a few people saw. Then someone else submitted another story and it took on a life of its own. It turned out that a lot of people got these emails. The researchers stated that they used the Tranco database of “popular” websites, and my tiny little site was only ranked as high as about number 350,000 in that list. I wasn’t alone. Princeton sent similar emails to other personal projects, and stories abounded that companies had hired counsel and incurred legal expenses to reply to complete fabrications. People had been frightened and were becoming angry.
Based on advice from Hacker News readers, I contacted Princeton’s Research Integrity & Compliance department and Institutional Review Board, and Radboud’s Research Data Management and Ethics Committee with my concerns. Radboud responded quickly. Princeton hasn’t responded.
What especially bothers me is that I think this is an important subject to study. I’m a Californian and I support the CCPA protecting my privacy. I want to know if companies are complying with their legal obligations, and I think a large research university like Princeton is the right kind of entity to conduct an effective study. I also believe that the researchers had the right intentions and wanted to do a good job. My problem with it is that I think they made a grave error in misrepresenting their legitimate research questions as coming from a fictional person, and wrote it in a way that set off a lot of “oh no, I think I’m about to be sued” alarms.
I suspect the data collected from misled responses is corrupted beyond repair. For instance, many entities who replied are likely to have formulated a policy solely because they received the email. I think, then, that the appropriate next steps for Princeton and Radboud are to immediately send explanation and apology emails to all the recipients of the original emails, and to delete all responses they received from recipients of the misleading messages.
This was such an unnecessary mess. It’s a shame because this could have been crafted in a way that resulted in better data and without scaring the research subjects. Do better next time, Princeton.
Update 2021-12-2: The researches updated their website to read, in part:
Our top priority has been issuing a one-time follow-up message that identifies our study and that recommends disregarding prior email. We are sending those messages.
We have also received consistent feedback encouraging us to promptly discard responses to study email. We agree, and we will delete all response data on December 31, 2021.
AirTag lost its way
Apple released their new AirTag product six months ago, and as competent as it is for finding lost gear, Apple’s done everything possible to hamstring the little device to make it frustrating to use.
The product idea is simple: you buy one and attach it to something you don’t want to misplace, like your car keys. Then you can use your iPhone to locate that thing when you inevitably misplace it. For that one specific use case, and if you live alone, AirTag is magical. The “Find My” app tells you how far and in what direction the lost device is so that you can walk right up to it. I’ve owned and used various Tile devices before, and AirTags are easier to use and work better. From a hardware standpoint, I can’t imagine what I’d improve about them. However, Apple’s software decisions are constraining the lovely hardware to the point that I don’t want to use it anymore.
All of AirTag’s problems come down to a single issue: Apple is afraid that someone will use an AirTag to stalk another person, to the point that they’ve deliberately encumbered it to near uselessness:
Apple claims that AirTags are meant for lost items, not stolen ones, but that’s a smokescreen for the fact that they haven’t figured out how to reconcile privacy with having the things work as expected. Despite their claims, of course they’re for recovering stolen items! If it weren’t for the disastrous software features, they’d be perfect for tracking down a purse thief or the person who stole your kid’s bike. Apple is selling a soup spoon, then acting shocked and dismayed when someone wants to use it to eat stew. If Apple can’t see why someone would naturally want to use an AirTag to get stolen things back, then that’s a telling failure of their imagination.
Anti-tracking features are good. No one wants to enable stalkers and I don’t blame Apple for that. However, they’re so paralyzed by even the possibility that someone might use an AirTag in a bad way that they’ve made it useless for a bunch of good ways. If Apple’s going to lock it down this hard, they shouldn’t have bothered releasing AirTag to the public. It would have been far less frustrating if it had never left the design lab.
I wanted to love AirTags, but I regret my purchases. It could have been a wonderful little gadget had Apple defined it by its possibilities instead of its limitations. I won’t be buying more.
GoDaddy Terminates Texas Spy Site
GoDaddy gives Texas abortion website notice: Find new host ASAP:
The highly controversial and regressive Texas abortion law went into effect on September 1. With the law comes the Texas Right to Life group’s website where anyone can submit allegations that a woman had an abortion past the state’s six-week cutoff mark. The state’s new abortion law also allows private citizens to target anyone accused of helping facilitate an abortion.
[…]
Amid the hacktivism is an outcry directed at GoDaddy, the company that hosts the website. Many have called on the company to cut off its services to Texas Right to Life, a call that has been heard. According to a statement GoDaddy provided to The New York Times, Texas Right to Life has been given 24 hours to find a different host for its website.
Even GoDaddy, of creepily sexy advertising fame, knows the Texas neighbor-stalking website is immoral.
I don’t ever want to hear another word about “government overreach” from the Texas GOP. Not a word.
What HIPAA's Privacy Rule Says
As someone who deals with HIPAA’s privacy compliance as part of my job, I don’t ever want to hear the word HIPAA again from someone who isn’t adjacent to healthcare. Almost no one understands what it is, but a hundred million people are explaining their wrong ideas of it to each other in a giant game of telephone.
Here’s a short summary of HIPAA’s Privacy Rule, as described by the U.S. Department of Health & Human Services:
Who it applies to: a healthcare provider such as a doctor or hospital, health plans, their business associates, and other people who manage patients’ healthcare information.
What it does: limit the information a covered entity can share about their patients to fulfill specific medical and business requirements.
What it doesn’t do: apply to anyone else except those covered entities; prevent you from sharing your own information; prevent others from asking you about your health, including vaccination status.
Anyone who says that doesn’t allow you to ask whether they’ve been vaccinated, or prevents them from answering, is factually wrong.
Opt-Out Tracking is an Awful Idea
Someone invented a new standardized way to opt out of telemetry for command line applications. This is a horrid idea.
The existence of the setting establishes “tracking is OK!” as the default, and makes opting out the responsibility of the end user. With this in place, if a company collects the names of all the files in my home directory, it’s my fault for not tweaking some random setting correctly. (For technical types: don’t forget to set the “don’t track me!” variable in your crontabs, or else they’ll run with tracking enabled! Be sure to add it to your sudoers file, or now root commands spy on you!)
If this should exist at all, it should be in the form of a “go ahead and spy on me!” whitelist, with all telemetry and other spyware disabled unless explicitly enabled. Then it becomes the responsibility of each application’s author to encourage their users to enable it. Or better, get over the bizarre and radical notion of enabling spyware in command line utilities.
Little League wants all your information
To sign kids up for our city’s Little League baseball program, you have to prove that they’re residents, which is reasonable. What’s not reasonable is the amount of information you have to provide on the registration website. You have to upload scans of a document in each of 3 categories:
Proof of Residency 1 Choose one of the following: Driver’s license, School records, Vehicle records, Employment records, Insurance documents
Proof of Residency 2 Choose one of the following: Welfare/child care records, Federal records, State records, Local records, Support payment records, Homeowner or tenant records, Military records
Proof of Residency 3 Choose one of the following: Voter’s registration, Utility bills, Financial records, Medical records, Internet, cable, or satellite bills
That alone is ripe for identity theft, but couple it with their privacy policy which includes this (emphasis mine):
Without limitation, this typically requires the use of certain personal information, including registration data, event data, and other personal information, to provide program information, special offers or services through Little League and/or its trusted sponsors, partners, or licensees, to fulfill your requests for information or products/services, to maintain a list of verified and eligible participants, to maintain a list of volunteers and provide them with the operating tools to manage leagues, or to respond to your inquiries about our programs.
In other words, you have to upload your most private information and agree to allow them to do as they like with it, including sharing it with whomever they like for any reason they choose.
This is unacceptable.
Update 2021-05-20
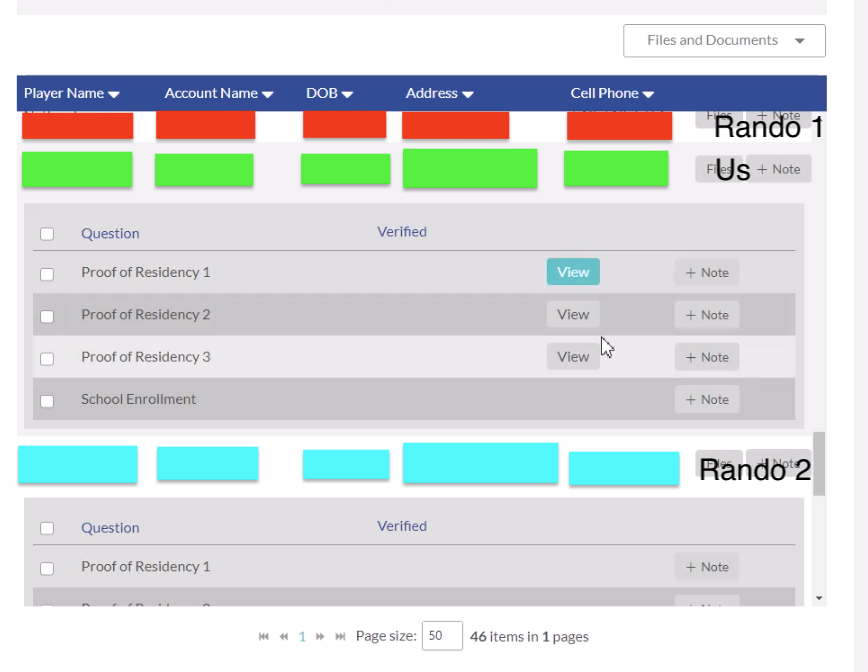
I contacted the company that manages Little League’s registrations and asked them to delete the documents I uploaded in order to sign up. They replied that their policy is to do that as soon as they’ve been evaluated. I asked the company to verify that they’d deleted our documents specifically. They replied with a video demonstrating that the files were no longer available. Great! The video included the PII of the families on either side of us on the list. Not great!
And that’s one big reason why I didn’t want to trust them with our information in the first place.
Search-proof your devices when traveling
Over-eager airport security has recently taken to making travelers unlock their phones and tablets for examination. This is both unforgivably invasive and trivially easy to defeat. Here’s how to protect your data1 on your iPhone or iPad2 when traveling.
Simplest: disable Touch ID
Now you have at least the physical ability to refuse to unlock your device. Be prepared for mental or legal pressure to supply your password, though. File this under “better than nothing”.
If you want to keep your current device
You’re traveling with a device, but one as bare as the day you originally bought it. Be prepared to explain why you’re carrying an empty device.
Keep your device, but less suspicious
Now you have a plausibly used device. When you get to your destination, reset your device again. Restore it from backup. This is more work than the previous instructions, but also less suspicious.
If you’d rather travel bare-handed
This is the most expensive option, but you can’t unlock what you don’t have.
Conclusion
Searching travelers’ devices at airports is security theater. It’s a massive and inconvenient violation of privacy, and only the world’s least prepared criminals would ever get caught this way. I guarantee I’m not the first person to think of backing up a phone and restoring it at my destination. Since it’s ineffective and almost certainly unconstitutional, cooler heads would recommend ending these pointless searches. Don’t wait for that to happen. Protect your data.
Purge your Yahoo account (but don't delete it!)
There are about 1.5 billion reasons to want to cancel your Yahoo account. Don’t do that!
According to Yahoo’s account deletion page, they “may allow other users to sign up for and use your current Yahoo! ID and profile names after your account has been deleted”:
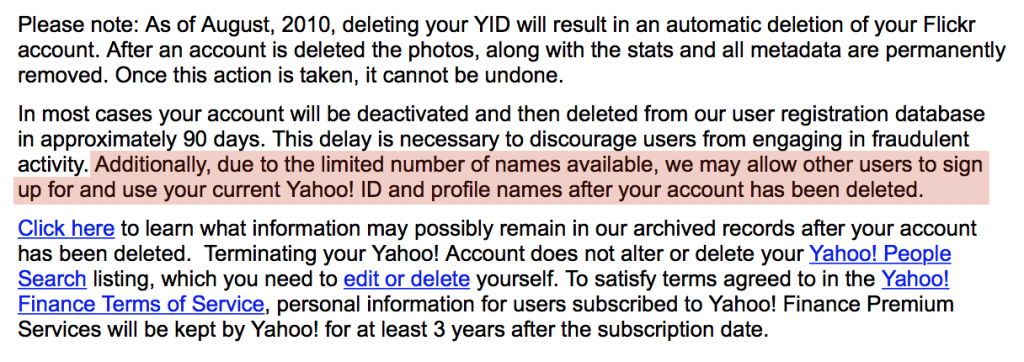
This is a terrible policy not shared by other service providers, and there are many scenarios where it’s a huge security problem for Yahoo’s users. For example:
Here’s what you should do instead:
Purge your Yahoo account
It’s time to move on. Yahoo has a terrible security track record and shows no signs of improving.
First, understand what you’ll be doing here. You’ll be removing everything from your Yahoo account: your email, contacts, events, and so on. Permanently. There’s no changing your mind. It’s extreme, sure, but until you do it’s likely that hackers can:
Don’t delete your account. Clean it out!
Secure it
Before doing anything else, change your Yahoo password! Hackers probably have your current one. I’m not exaggerating.
Once that’s done, turn on two-factor authentication (2FA). This can prevent hackers from accessing your account even if they get your password.
Once that’s done, make a note to yourself to turn on 2FA for every other account you have that supports it.
Make your new home
Before you start, you’ll want to create an email account with a new provider. Lots of people like Gmail but pick one that looks good to you. This will be your new home account on the Internet: the email address that you give out to friends and coworkers and that you use to log into websites.
Clear your email
Clear everything else
If you’re like most people, that’s probably 99% of your Yahoo data. You’re not quite done yet, though! Now click through each of the services in the little icons in the top left corner:

They all may have more information stored in them. Each works a little differently but you should be able to figure out how to clean out each one.
Set a vacation reminder
Other email providers make it easy to forward all of your incoming mail to a new account. Yahoo removed that feature recently so you can’t use that convenient approach. Instead, you’ll make a Vacation Response to tell people about your new address.
I may now be reached at me@example.com. Please update your address book. Thanks!
Now anyone writing to you will get a message with your new address, but their email will still land in your Yahoo inbox.
Change your logins
Now go through your web accounts and change all of them where you log in with me@yahoo.com to use your new email address instead. If you use a password manager to keep track of your accounts, this will be easy. Time consuming — thanks, Yahoo! — but easy.
Check back
You’re going to miss a few accounts, and some friends or family will stubbornly insist on sending email to your old address. Set a reminder or mark your calendar to check your Yahoo mail a month from now to see who’s written to you. Update each of those people or accounts, then delete all of your new messages. Check again in another month and then another after that. Eventually this will slow to a trickle and you can forget about your old Yahoo account for many months at a time (or until the next news article about a giant Yahoo hack comes along, and then you can smile to yourself because it doesn’t affect you anymore).
Conclusion
Migrating off Yahoo is a pain in the neck. Google, in contrast, makes it easy to extract all your information and then securely close your account. Yahoo does not. It won’t be quick or painless, but I recommend that you start now.